 Admin
Admin 2017-02-24 11:01:51
2017-02-24 11:01:51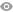
组网需求
如图1-1所示,总部和分支网关分别通过NGFW和ASA设备接入Internet。总部需要将通过IPSec隧道传输的流量全部引入到Tunnel接口,便于对经过IPSec隧道传输的流量进行管理,以实现分支和总部内网安全互通。
图1-1 NGFW以Tunnel接口方式与Cisco网关建立IPSec隧道

配置项 | NGFW | ASA | |
设备信息 | l 设备型号:USG6330 l 软件版本:V100R001C30 | l 设备型号:ASA5520-K8 l 软件版本:9.1 | |
IPSec安全提议 | 封装模式 | 隧道模式 | 隧道模式 |
安全协议 | ESP | ESP | |
ESP协议验证算法 | SHA1 | ESP-SHA-HMAC | |
ESP协议加密算法 | AES | ESP-AES | |
IKE对等体 | 协商模式 | 主模式 | 主模式 |
加密算法 | AES-128 | AES | |
认证算法 | SHA1 | SHA | |
DH Group | GROUP2 | GROUP 2 | |
预共享密钥 | Key123 | Key123 | |
身份类型 | IP地址 | IP地址 | |
版本 | V1 | V1 | |
操作步骤
步骤 1 配置NGFW。
1. 配置接口IP地址,并将接口加入安全区域。
[NGFW] interface GigabitEthernet 1/0/1
[NGFW-GigabitEthernet1/0/1] ip address 10.1.1.1 24
[NGFW-GigabitEthernet1/0/1] ip service-manage ping permit /*允许ASA设备ping此接口。*/
[NGFW-GigabitEthernet1/0/1] quit
[NGFW] interface GigabitEthernet 1/0/2
[NGFW-GigabitEthernet1/0/2] ip address 1.1.3.1 24
[NGFW-GigabitEthernet1/0/2] service-manage ping permit /*允许ASA设备ping此接口。*/
[NGFW-GigabitEthernet1/0/2] quit
[NGFW] interface tunnel 1
[NGFW-Tunnel1] ip address unnumbered interface GigabitEthernet1/0/2
[NGFW-Tunnel1] tunnel-protocol ipsec
[NGFW-Tunnel1] service-manage ping permit
[NGFW-Tunnel1] quit
[NGFW] firewall zone trust
[NGFW-zone-trust] add interface GigabitEthernet 1/0/1
[NGFW-zone-trust] quit
[NGFW] firewall zone untrust
[NGFW-zone-untrust] add interface GigabitEthernet 1/0/2
[NGFW-zone-untrust] add interface tunnel 1
[NGFW-zone-untrust] quit
2. 配置域间安全策略。
a. 配置Trust域与Untrust域的安全策略,允许IPSec封装前和解封装后的原始报文能通过NGFW。
[NGFW] security-policy
[NGFW-policy-security] rule name 1
[NGFW-policy-security-rule-1] source-zone untrust
[NGFW-policy-security-rule-1] destination-zone trust
[NGFW-policy-security-rule-1] source-address 10.1.3.0 24
[NGFW-policy-security-rule-1] destination-address 10.1.1.0 24
[NGFW-policy-security-rule-1] action permit
[NGFW-policy-security-rule-1] quit
[NGFW-policy-security] rule name 2
[NGFW-policy-security-rule-2] source-zone trust
[NGFW-policy-security-rule-2] destination-zone untrust
[NGFW-policy-security-rule-2] source-address 10.1.1.0 24
[NGFW-policy-security-rule-2] destination-address 10.1.3.0 24
[NGFW-policy-security-rule-2] action permit
[NGFW-policy-security-rule-2] quit
b. 配置Local域与Untrust域的安全策略,允许IKE协商报文能正常通过NGFW。
[NGFW-policy-security] rule name 3
[NGFW-policy-security-rule-3] source-zone local
[NGFW-policy-security-rule-3] destination-zone untrust
[NGFW-policy-security-rule-3] source-address 1.1.3.1 32
[NGFW-policy-security-rule-3] destination-address 1.1.5.1 32
[NGFW-policy-security-rule-3] action permit
[NGFW-policy-security-rule-3] quit
[NGFW-policy-security] rule name 4
[NGFW-policy-security-rule-4] source-zone untrust
[NGFW-policy-security-rule-4] destination-zone local
[NGFW-policy-security-rule-4] source-address 1.1.5.1 32
[NGFW-policy-security-rule-4] destination-address 1.1.3.1 32
[NGFW-policy-security-rule-4] action permit
[NGFW-policy-security-rule-4] quit
3. 配置IPSec策略。
a. 配置访问控制列表,定义需要保护的数据流。
[NGFW]acl 3000
[NGFW-acl-adv-3000]rule permit ip source 10.1.1.0 0.0.0.255 destination 10.1.3.0 0.0.0.255
[NGFW-acl-adv-3000]quit
b. 配置IPSec安全提议。
[NGFW] ipsec proposal tran1
[NGFW-ipsec-proposal-tran1] transform esp
[NGFW-ipsec-proposal-tran1] encapsulation-mode tunnel
[NGFW-ipsec-proposal-tran1] esp authentication-algorithm sha1
[NGFW-ipsec-proposal-tran1] esp encryption-algorithm aes-128
[NGFW-ipsec-proposal-tran1] quit
c. 创建IKE安全提议。
[NGFW] ike proposal 1
[NGFW-ike-proposal-1] encryption-algorithm aes-128
[NGFW-ike-proposal-1] authentication-algorithm sha1
[NGFW-ike-proposal-1] dh group2
[NGFW-ike-proposal-1] quit
d. 配置IKE对等体。
[NGFW] ike peer asa
[NGFW-ike-peer-asa] undo version 2
[NGFW-ike-peer-asa] exchange-mode main
[NGFW-ike-peer-asa] ike-proposal 1
[NGFW-ike-peer-asa] remote-address 1.1.5.1
[NGFW-ike-peer-asa] pre-shared-key Key123
[NGFW-ike-peer-asa] quit
e. 配置isakmp方式的IPSec策略。
[NGFW] ipsec policy map1 1 isakmp
[NGFW-ipsec-policy-isakmp-map1-1] security acl 3000
[NGFW-ipsec-policy-isakmp-map1-1] proposal tran1
[NGFW-ipsec-policy-isakmp-map1-1] ike-peer asa
[NGFW-ipsec-policy-isakmp-map1-1] quit
f. 在Tunnel接口上应用IPSec策略。
[NGFW] interface Tunnel 1
[NGFW-Tunnel1] ipsec policy map1
[NGFW-Tunnel1] quit
4. 配置路由。
# 配置到分支内网的路由,并将流量引流到Tunnel接口。
[NGFW] ip route-static 10.1.3.0 24 tunnel 1
# 配置到NGFW连接到Internet的缺省路由,假设下一跳为1.1.3.2。
[NGFW] ip route-static 0.0.0.0 0.0.0.0 1.1.3.2
步骤 2 配置ASA设备。
1. 配置ASA接口的IP地址。
ASA5520> en
ASA5520# configure terminal
ASA5520(config)# interface GigabitEthernet 0/1
ASA5520(config-if)# nameif in
ASA5520(config-if)# security-level 90
ASA5520(config-if)# ip address 10.1.3.1 255.255.255.0
ASA5520(config-if)# exit
ASA5520(config)# interface interface GigabitEthernet 0/2
ASA5520(config-if)# nameif out
ASA5520(config-if)# security-level 10
ASA5520(config-if)# ip address 1.1.5.1 255.255.255.0
ASA5520(config-if)# exit
2. 打开ASA接口的访问控制。
ASA5520(config)# access-list 10 extended permit icmp any any
ASA5520(config)# access-group 10 in interface in
ASA5520(config)# access-group 10 out interface in
ASA5520(config)# access-group 10 in interface out
ASA5520(config)# access-group 10 out interface out
3. 配置ASA到Internet的缺省路由,假设下一跳地址为1.1.5.2。
ASA5520(config)# route out 0.0.0.0 0.0.0.0 1.1.5.2 1
4. 配置IPSec。
a. 配置ACL(访问控制列表),定义需要保护的数据流。
这里需要注意,Cisco这里的ACL用的是掩码,而HUAWEI设备用的是反掩码,两者存在不同。
ASA5520(config)# access-list ipsec permit ip 10.1.3.0 255.255.255.0 10.1.1.0 255.255.255.0
b. 配置IPSec安全提议。
ASA5520(config)# crypto ipsec transform-set myset esp-aes esp-sha-hmac
c. 创建IKE安全提议。
ASA5520(config-isakmp-policy)# crypto isakmp policy 10
ASA5520(config-isakmp-policy)# authentication pre-share
ASA5520(config-isakmp-policy)# encryption aes
ASA5520(config-isakmp-policy)# hash sha
ASA5520(config-isakmp-policy)# group 2
ASA5520(config-isakmp-policy)# lifetime 86400
d. 配置预共享密钥。
ASA5520(config)# crypto isakmp key Key123 address 1.1.3.1
e. 配置IPSec策略。
在IPSec策略中引用前面配置的ACL、IPSec安全提议。
ASA5520(config)# crypto map ipsec_map 10 match address ipsec
ASA5520(config)# crypto map ipsec_map 10 set peer 1.1.3.1
ASA5520(config)# crypto map ipsec_map 10 set transform-set myset
f. 在接口上应用IPSec策略。
ASA5520(config)# crypto map ipsec_map interface out
g. 在接口上启用IPSec策略。
ASA5520(config)# crypto isakmp enable out
----结束
结果验证
1. 配置完成后,使用分支下的用户Ping总部下的用户。
2. 正常情况下,分支访问总部的数据流将会触发两台网关之间建立IPSec隧道。
此处在NGFW上查看IKE SA的建立情况,可以看到IKE SA已经建立成功。
<NGFW> display ike sa
15:53:30 2015/12/26
--------------------------------------------------------------------------------------------------
conn-id peer flag phase vpn
--------------------------------------------------------------------------------------------------
54 1.1.5.1 RD|ST|A v1:2 public
53 1.1.5.1 RD|ST|A v1:1 public
flag meaning
RD--READY ST--STAYALIVE RL--REPLACED FD--FADING TO--TIMEOUT
TD--DELETING NEG--NEGOTIATING D--DPD M--ACTIVE S--STANDBY
A--ALONE
3. 使用display ipsec sa命令查看IPSec的建立情况,可以看到IPSec SA也已建立成功。
<NGFW> display ipsec sa
15:53:53 2015/12/26
===============================
Interface: Tunnel1
path MTU: 1500
===============================
-----------------------------
IPsec policy name: "map1"
sequence number: 1
mode: isakmp
vpn: public
-----------------------------
connection id: 54
rule number: 5
encapsulation mode: tunnel
holding time: 0d 0h 27m 23s
tunnel local : 1.1.3.1 tunnel remote: 1.1.5.1
flow source: 10.1.1.0/255.255.255.0 0/0
flow destination: 10.1.3.0/255.255.255.0 0/0
[inbound ESP SAs]
spi: 4231227848 (0xfc3369c8)
vpn: public said: 8 cpuid: 0x0000
proposal: ESP-ENCRYPT-AES ESP-AUTH-SHA1
sa remaining key duration (kilobytes/sec): 4608000/1957
max received sequence-number: 3
udp encapsulation used for nat traversal: N
[outbound ESP SAs]
spi: 2527152779 (0x96a14a8b)
vpn: public said: 9 cpuid: 0x0000
proposal: ESP-ENCRYPT-AES ESP-AUTH-SHA1
sa remaining key duration (kilobytes/sec): 4608000/1957
max sent sequence-number: 4
udp encapsulation used for nat traversal: N